on
Webinar Notes // Domestic Extremism: What Security Teams Should Know
Speaker
Dr. Jennifer Hesterman is a retired Air Force colonel, serving in three Pentagon tours and commanding in the field multiple times. Her final assignment was Vice Commander, Andrews Air Force Base, Maryland, where she led installation security and protection of Air Force One, force support, and the 1st Helicopter Squadron. She regularly met and escorted the President and other heads of state on the airfield. She is the recipient of the Legion of Merit, the Meritorious Service medal with 5 oak leaf clusters and the Global War on Terrorism medal, among others.
A counterterrorism and soft target hardening expert, she is presently Vice President at Watermark Risk Management International and instructs graduate-level security courses for the Defense Counterintelligence and Security Agency. She also advises the Homeland Security Training Institute at the College of DuPage and the Crisis Response Journal.
Dr. Hesterman is a sought after consultant and trainer, supporting the DHS, the FBI, DoD, US Secret Service, the Department of Transportation, state and local law enforcement, Fortune 100s, Major League Baseball and soft target locations and mass gathering events.
She holds a doctoral degree from Benedictine University, Master of Science degrees from Johns Hopkins University and Air University, and a Bachelor of Science from Penn State University. She was a National Defense Fellow at the Center for Strategic and International Studies; is an alumnus of the Harvard Senior Executive Fellows program and was a fellow at the Center for Cyber and Homeland Security at George Washington University.
An academic author for Taylor & Francis Group, her book Soft Target Hardening: Protecting People from Attack was the ASIS Security Industry Book of the Year for 2015. The second edition received the same honors in 2019, and was the Social Sciences Book of the Year for Taylor & Francis. She also authored Soft Target Crisis Management (2016) and The Terrorist-Criminal Nexus (2013) and published 32 articles in a variety of journals and security magazines.
The host was a company called Topo.ai. They briefly talked about their product.
Notes

- What drives a rational person towards radical ideologies/groups?
- Instinct Theory: Behavior is a function of a person’s instinct rather than conscious, purposeful and rational activities.
- Reinforcement Theory: Person’s current behavior strongly affected by knowledge of rewards for similar past behaviors.
- Cognitive Theory: Behaviour is not much a function of consequences, as it is a person’s future belief and expectations.
- Need for Affiliation
- Maslow’s hierarchy of needs.
- Anxiety and stress feeds
- The pandemic fed the beast
- A deconstructured ideology must be replaced with something else… Herein lies the dilemma.
- Group gives members an identity and demands (or subtly elicits) loyalty for the sense of security imparted.
- Group culture:
- Values
- Norms
- Artifacts: Rituals, places, dates, symbols, colors, dress
- Environment: Closed system or open?
- Nonviolent Extremism
- Radical preaching, writing, think tanks
- Inspiring, inciting, recruiting, boosting morale, fundraising
- Violent Extremism
- Perception of being marginalized, discriminated against, ridiculed, persecuted
- Convert or eliminate
- Maybe the violent actor has grievances and seeks revenge or is coercede, paid, manipulated, or shamed into participating but eventually original “hook” evolves into greed. Sometimes violent extremism becomes a career.
- The internet accelerates the speed of radicalization, provides interface between recruiters/recruits and gives 24/7 access to tactical info.
- Online Recruitment Strategy:
- Seek out
- Isolate
- Encourage
- Can take months, years or days.
- Example: Ohio State attacker
- Extremism in the U.S.
- Right Wing: neo-Nazism, neo-fascism, white nationalism, religious nationalism, anti-government patriots, militias, sovereign citizens
- Left Wing: Revolutionary socialism, antifascism, anarchism
- Religious: Most dangerous - apocalyptic, martyrs
- Single Interest: Animals, plant life, climate change
- Wildcards: Male supremacism (incel, misogynist), ad hoc groups like the Proud Boys, Boogaloo Bois
- Boogaloo Bois is interesting as it has supporters from different segments like BLM supporters, right-wing, incels all against the government. From Meme to Movement to Murder. News
- Domestic Violent Extremists (DVE) of Greatest Concern
- QAnon conspiracy theorists
- Anarchist extremists
- Militia extremists
- DHS CT Insights
- Most significant terrorist threat to the US are lone actors or small groups based on an ideological group they connect with online - combination of beliefs and personal grievances.
- Threat comes from people who have a superficial understanding of the ideology. They are angry, disconnected, treated unfairly, and participating in these groups provides a sense of self-worth.
- Lone Actor Terror (LAT)
- Individuals who prepare for and execute violence without external assistance.
- Despite ad hoc nature and limited resources, can mount high-profile, extremely destructive attacks.
- Two types:
- Well adapted to society - makes a tactical choice to engage in lone actor ops; leaves society
- Not well adapted, suffering mental health issues or in psychological distress; society leaves them
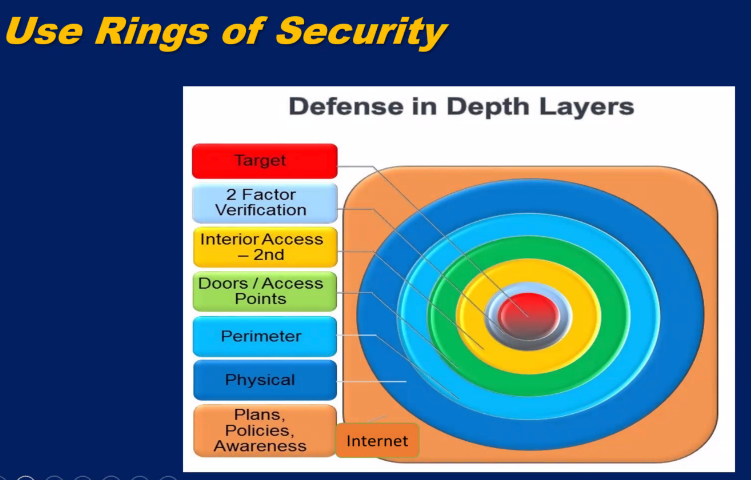
- Protests or acts of violence may put your organization in the crosshairs - you must continuously assess the threat. Your ability to deter attack is amplified by understanding vulnerability.
- Find your Achilles Heel and cover it.
- Divert/off-road: Conceal, cover, disguise; lower the heat.
- Deter:
- Use security language on your websites, social media.
- Display robust security signage and have a security presence.
- Deceive: Physical deception tactics - look harder than you are.
- Remember: The best defense is a good offense.
- The NITTF defines the 5 categories of Insider Threat as:
- Leaks
- Spills
- Espionage
- Sabotage
- Targeted Violence
- Many known insider threats have been associated with one or more of the following behavioral indicators:
- Significant changes in personality, behavior, or work habits
- Substance abuse or addictive behaviors
- Financial change
- Disgruntled to the point of wanting to retaliate
- Disaffection, marginalization, alienation
- Disregard for security procedures and protocols
- Ideations on social media and/or in the workplace
- The Fifth Column means a group or people sympathetic to or working for adversaries.
- Be attune to the “human condition”.
- Access large body of academic thought on violent extremism.
- Stay abreast of current groups, activities, targets and tactics then adjust your security plans.
- Dr. Hesterman has a book called Soft Target Hardening: Protecting People from Attack
Resources suggested by Dr. Hesterman
- Slavoj Zizek, The Sublime Object of Ideology, 1989 (London: Verso)
- Images of Organization, Gareth Morgan (2006)
- The Starfish and the Spider: The Unstoppable Power of Leaderless Organizations, Ori Brafman and Rod Beckstrom (2006)
- Dr. Alex Schmid, Violent and Non-Violent Extremism: Two Sides of the Same Coin? (2014)
- National Strategy for Countering Domestic Terrorism
- ICCT project: Countering Lone Actor Terrorism
- The Age of Lone Wolf Terrorism, Spaaij & Hamm, Columbia University Press (2017)
- FBI - Terrorism Vulnerability Self-Assessment Checklist
- DNI NTTF
- Managing the Insider Threat: No Dark Corners, Nick Catrantzos